k6 Load Generator
Introduction¶
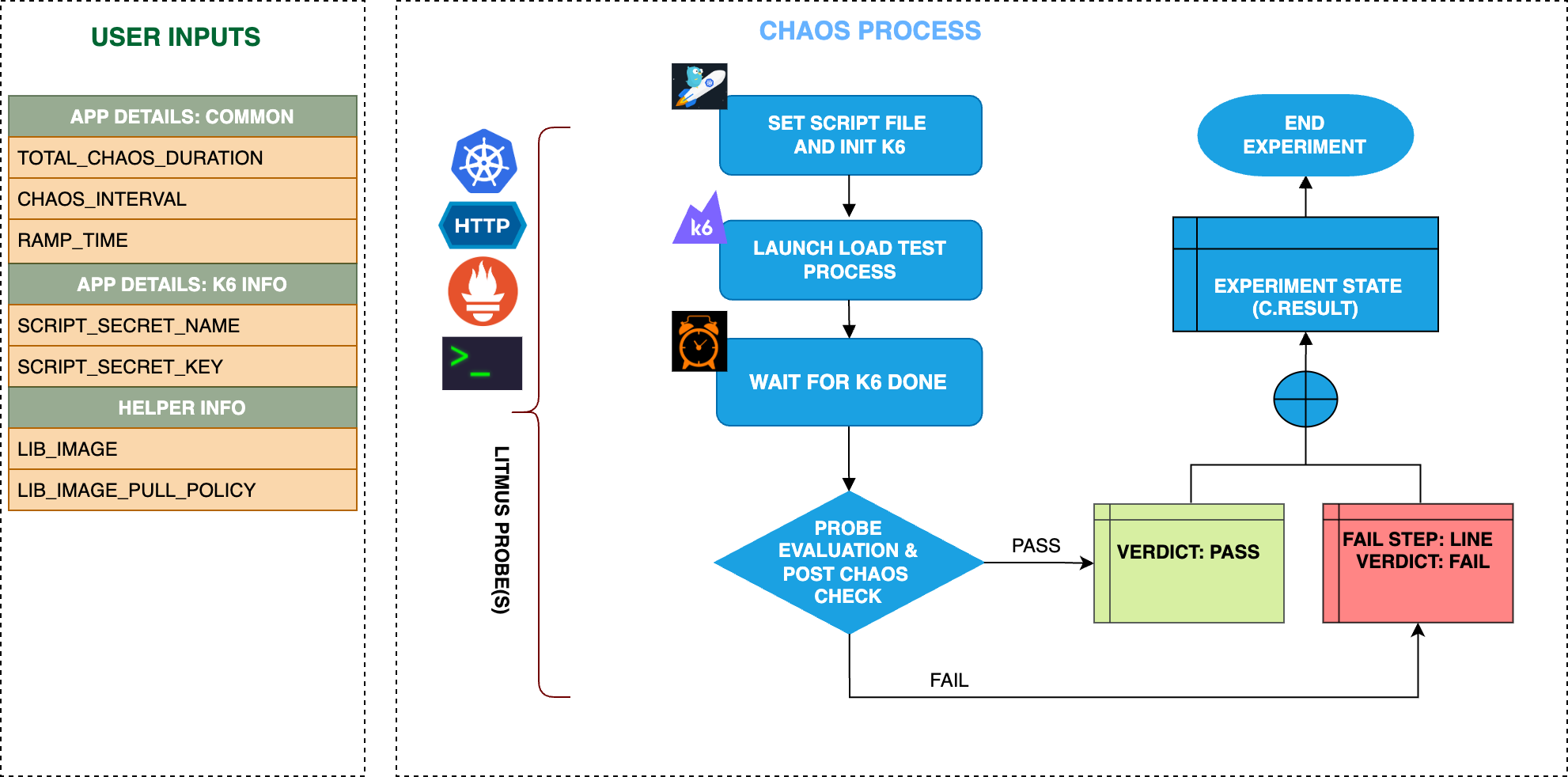
k6 loadgen fault simulates load generation on the target hosts for a specific chaos duration. This fault: - Slows down or makes the target host unavailable due to heavy load. - Checks the performance of the application or process running on the instance. Support various types of load testing (ex. spike, smoke, stress)
Scenario: Load generating with k6
Uses¶
View the uses of the experiment
Prerequisites¶
Verify the prerequisites
- Ensure that Kubernetes Version > 1.16
- Ensure that the Litmus Chaos Operator is running by executing
kubectl get podsin operator namespace (typically,litmus). If not, install from here - Ensure to create a Kubernetes secret having the JS script file in the
Chaos Infrastructure's namespace (litmusby default). The simplest way to create a secret object looks like this:kubectl create secret generic k6-script \ --from-file=<<script-path>> -n <<chaos_infrastructure_namespace>>
Minimal RBAC configuration example (optional)¶
NOTE
If you are using this experiment as part of a litmus workflow scheduled constructed & executed from chaos-center, then you may be making use of the litmus-admin RBAC, which is pre installed in the cluster as part of the agent setup.
View the Minimal RBAC permissions
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: k6-loadgen-sa
namespace: default
labels:
name: k6-loadgen-sa
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: k6-loadgen-sa
namespace: default
labels:
name: k6-loadgen-sa
rules:
- apiGroups: ["","litmuschaos.io","batch","apps"]
resources: ["pods","configmaps","jobs","pods/exec","pods/log","events","chaosengines","chaosexperiments","chaosresults"]
verbs: ["create","list","get","patch","update","delete","deletecollection"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: k6-loadgen-sa
namespace: default
labels:
name: k6-loadgen-sa
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: k6-loadgen-sa
subjects:
- kind: ServiceAccount
name: k6-loadgen-sa
namespace: default
Experiment tunables¶
check the experiment tunables
Optional Fields
| Variables | Description | Notes |
|---|---|---|
| TOTAL_CHAOS_DURATION | The time duration for chaos injection (seconds) | Defaults to 20s |
| CHAOS_INTERVAL | Time interval b/w two successive k6-loadgen (in sec) | If the CHAOS_INTERVAL is not provided it will take the default value of 10s |
| RAMP_TIME | Period to wait before injection of chaos in sec | |
| LIB_IMAGE | LIB Image used to excute k6 engine | Defaults to ghcr.io/grafana/k6-operator:latest-runner |
| LIB_IMAGE_PULL_POLICY | LIB Image pull policy | Defaults to Always |
| SCRIPT_SECRET_NAME | Provide the k8s secret name of the JS script to run k6. | Default value: k6-script |
| SCRIPT_SECRET_KEY | Provide the key of the k8s secret named SCRIPT_SECRET_NAME | Default value: script.js |
Experiment Examples¶
Common and Pod specific tunables¶
Refer the common attributes and Pod specific tunable to tune the common tunables for all experiments and pod specific tunables.
Custom k6 configuration¶
You can add k6 options(ex hosts, thresholds) in the script options object. More details can be found here
Custom Secret Name and Secret Key¶
You can provide the secret name and secret key of the JS script to be used for k6-loadgen. The secret should be created in the same namespace where the chaos infrastructure is created. For example, if the chaos infrastructure is created in the litmus namespace, then the secret should also be created in the litmus namespace.
You can write a JS script like below. If you want to know more about the script, checkout this documentation.
import http from 'k6/http';
import { sleep } from 'k6';
export const options = {
vus: 100,
duration: '30s',
};
export default function () {
http.get('http://<<target_domain_name>>/');
sleep(1);
}
Then create a secret with the above script.
kubectl create secret generic custom-k6-script \
--from-file=custom-script.js -n <<chaos_infrastructure_namespace>>
And If we want to use custom-k6-script secret and custom-script.js as the secret key, then the experiment tunable will look like this:
---
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: nginx-chaos
namespace: default
spec:
engineState: 'active'
chaosServiceAccount: litmus-admin
experiments:
- name: k6-loadgen
spec:
components:
env:
# set chaos duration (in sec) as desired
- name: TOTAL_CHAOS_DURATION
value: "30"
# Interval between chaos injection in sec
- name: CHAOS_INTERVAL
value: "30"
# Period to wait before and after injection of chaos in sec
- name: RAMP_TIME
value: "0"
# Provide the secret name of the JS script
- name: SCRIPT_SECRET_NAME
value: "custom-k6-script"
# Provide the secret key of the JS script
- name: SCRIPT_SECRET_KEY
value: "custom-script.js"
# Provide the image name of the helper pod
- name: LIB_IMAGE
value: "ghcr.io/grafana/k6-operator:latest-runner"
# Provide the image pull policy of the helper pod
- name: LIB_IMAGE_PULL_POLICY
value: "Always"