Node Restart
Introduction¶
- It causes chaos to disrupt state of node by restarting it.
- It tests deployment sanity (replica availability & uninterrupted service) and recovery workflows of the application pod
Scenario: Restart the node
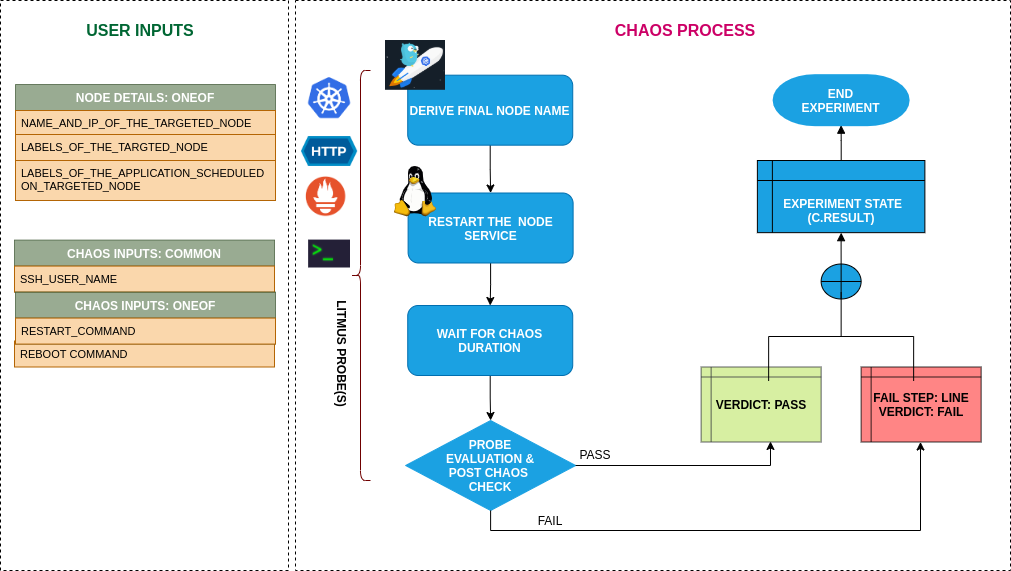
Uses¶
View the uses of the experiment
coming soon
Prerequisites¶
Verify the prerequisites
- Ensure that Kubernetes Version > 1.16
- Ensure that the Litmus Chaos Operator is running by executing
kubectl get podsin operator namespace (typically,litmus).If not, install from here - Ensure that the
node-restartexperiment resource is available in the cluster by executingkubectl get chaosexperimentsin the desired namespace. If not, install from here -
Create a Kubernetes secret named
id-rsawhere the experiment will run, where its contents will be the private SSH key forSSH_USERused to connect to the node that hosts the target pod in the secret fieldssh-privatekey. A sample secret is shown below:apiVersion: v1 kind: Secret metadata: name: id-rsa type: kubernetes.io/ssh-auth stringData: ssh-privatekey: |- # SSH private key for ssh contained here
Creating the RSA key pair for remote SSH access should be a trivial exercise for those who are already familiar with an ssh client, which entails the following actions:
- Create a new key pair and store the keys in a file named
my-id-rsa-keyandmy-id-rsa-key.pubfor the private and public keys respectively:ssh-keygen -f ~/my-id-rsa-key -t rsa -b 4096 - For each node available, run this following command to copy the public key of
my-id-rsa-key:ssh-copy-id -i my-id-rsa-key user@node
For further details, please check this documentation. Once you have copied the public key to all nodes and created the secret described earlier, you are ready to start your experiment.
Default Validations¶
View the default validations
The target nodes should be in ready state before and after chaos injection.
Minimal RBAC configuration example (optional)¶
NOTE
If you are using this experiment as part of a litmus workflow scheduled constructed & executed from chaos-center, then you may be making use of the litmus-admin RBAC, which is pre installed in the cluster as part of the agent setup.
View the Minimal RBAC permissions
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: node-restart-sa
namespace: default
labels:
name: node-restart-sa
app.kubernetes.io/part-of: litmus
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: node-restart-sa
labels:
name: node-restart-sa
app.kubernetes.io/part-of: litmus
rules:
# Create and monitor the experiment & helper pods
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update", "deletecollection"]
# Performs CRUD operations on the events inside chaosengine and chaosresult
- apiGroups: [""]
resources: ["events"]
verbs: ["create","get","list","patch","update"]
# Fetch configmaps & secrets details and mount it to the experiment pod (if specified)
- apiGroups: [""]
resources: ["configmaps","secrets"]
verbs: ["get","list",]
# Track and get the runner, experiment, and helper pods log
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
# for creating and managing to execute comands inside target container
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["get","list","create"]
# for configuring and monitor the experiment job by the chaos-runner pod
- apiGroups: ["batch"]
resources: ["jobs"]
verbs: ["create","list","get","delete","deletecollection"]
# for creation, status polling and deletion of litmus chaos resources used within a chaos workflow
- apiGroups: ["litmuschaos.io"]
resources: ["chaosengines","chaosexperiments","chaosresults"]
verbs: ["create","list","get","patch","update","delete"]
# for experiment to perform node status checks
- apiGroups: [""]
resources: ["nodes"]
verbs: ["get","list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: node-restart-sa
labels:
name: node-restart-sa
app.kubernetes.io/part-of: litmus
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: node-restart-sa
subjects:
- kind: ServiceAccount
name: node-restart-sa
namespace: default
Use this sample RBAC manifest to create a chaosServiceAccount in the desired (app) namespace. This example consists of the minimum necessary role permissions to execute the experiment.
Experiment tunables¶
check the experiment tunables
Mandatory Fields
| Variables | Description | Notes |
|---|---|---|
| TARGET_NODE | Name of target node, subjected to chaos. If not provided it will select the random node | |
| NODE_LABEL | It contains node label, which will be used to filter the target node if TARGET_NODE ENV is not set | It is mutually exclusive with the TARGET_NODE ENV. If both are provided then it will use the TARGET_NODE |
Optional Fields
| Variables | Description | Notes |
|---|---|---|
| LIB_IMAGE | The image used to restart the node | Defaults to litmuschaos/go-runner:latest |
| SSH_USER | name of ssh user | Defaults to root |
| TARGET_NODE_IP | Internal IP of the target node, subjected to chaos. If not provided, the experiment will lookup the node IP of the TARGET_NODE node |
Defaults to empty |
| REBOOT_COMMAND | Command used for reboot | Defaults to sudo systemctl reboot |
| TOTAL_CHAOS_DURATION | The time duration for chaos insertion (sec) | Defaults to 30s |
| RAMP_TIME | Period to wait before and after injection of chaos in sec | |
| LIB | The chaos lib used to inject the chaos | Defaults to litmus supported litmus only |
Experiment Examples¶
Common and Node specific tunables¶
Refer the common attributes and Node specific tunable to tune the common tunables for all experiments and node specific tunables.
Reboot Command¶
It defines the command used to restart the targeted node. It can be tuned via REBOOT_COMMAND ENV.
Use the following example to tune this:
# provide the reboot command
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: node-restart-sa
experiments:
- name: node-restart
spec:
components:
env:
# command used for the reboot
- name: REBOOT_COMMAND
value: 'sudo systemctl reboot'
# name of the target node
- name: TARGET_NODE
value: 'node01'
- name: TOTAL_CHAOS_DURATION
value: '60'
SSH User¶
It defines the name of the SSH user for the targeted node. It can be tuned via SSH_USER ENV.
Use the following example to tune this:
# name of the ssh user used to ssh into targeted node
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: node-restart-sa
experiments:
- name: node-restart
spec:
components:
env:
# name of the ssh user
- name: SSH_USER
value: 'root'
# name of the target node
- name: TARGET_NODE
value: 'node01'
- name: TOTAL_CHAOS_DURATION
value: '60'
Target Node Internal IP¶
It defines the internal IP of the targeted node. It is an optional field, if internal IP is not provided then it will derive the internal IP of the targeted node. It can be tuned via TARGET_NODE_IP ENV.
Use the following example to tune this:
# internal ip of the targeted node
apiVersion: litmuschaos.io/v1alpha1
kind: ChaosEngine
metadata:
name: engine-nginx
spec:
engineState: "active"
annotationCheck: "false"
chaosServiceAccount: node-restart-sa
experiments:
- name: node-restart
spec:
components:
env:
# internal ip of the targeted node
- name: TARGET_NODE_IP
value: '<ip of node01>'
# name of the target node
- name: TARGET_NODE
value: 'node01'
- name: TOTAL_CHAOS_DURATION
value: '60'